Hackers exploit SourceForge to hide crypto miners in Microsoft Office packages

Cybercriminals are abusing SourceForge’s project domains to spread trojanized Office installers embedded with cryptocurrency mining tools and clipboard hijackers.
A newly uncovered malware campaign is turning SourceForge’s infrastructure into a launchpad for infection, leveraging the platform’s developer-friendly tools to trick users into downloading malicious crypto software.
According to researchers at Kaspersky, the scheme specifically targets crypto users by disguising malware as office-related downloads — complete with bloated installers, password-protected archives, and layers of obfuscation that eventually deliver a crypto miner and a ClipBanker to hijack crypto transactions.
In a blog post on Tuesday, April 8, researchers said the attackers set up a fake project on SourceForge called “officepackage,” made to look like Microsoft Office add-ins copied from GitHub. While the project page itself might look normal, the real trap was its auto-generated subdomain “officepackage.sourceforge.io,” the researchers noted. Search engines like Russia‘s Yandex picked it up, and when users visited the page, they saw a fake list of office apps with download buttons that actually started the malware infection.
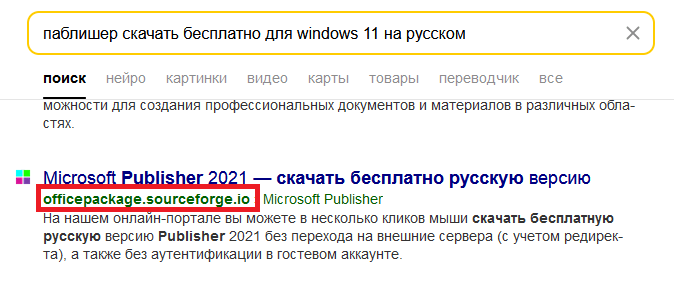
Clicking the fake download links sends users through several redirects before delivering a small zip file. But once unzipped, it expands into a bloated 700MB installer.
When launched, the installer uses hidden scripts to grab more files from GitHub, eventually unpacking malware that checks for antivirus tools before running. If no threats are detected, it installs tools like AutoIt and Netcat — one script sends system info to a Telegram bot, while another ensures the crypto-mining malware stays on the system, the researchers say.
Kaspersky says 90% of affected users appear to be in Russia, with over 4,600 hits between January and March. While the campaign primarily seeks to steal crypto funds, researchers warn that infected machines may also be sold to other threat actors.