Bitcoin Core Bug Resolved in 0.16.3 Client: Threatened Security of Lightning Network

A GitHub report opened on September 17, 2018, revealed a recent bug in the Bitcoin Core versions 0.14.0 to 0.16.2. The exploit threatened to crash Bitcoin Core if the most recent version wasn’t updated. The anonymous reporter reached out to developers of the pioneer cryptocurrency with their findings, after which Anthony Towns, Hennadii Stepanov, Matt Corallo, Suhas Daftuar, Wladimir J. van der Laan, and a handful of others went to work on releasing version 0.16.3 of the client.
Double-Spending Attack
The details of the exploit reveal that the network was vulnerable to a denial-of-service attack. Malicious miners were allowed “to validate a block containing a transaction that [attempted] to spend the same input twice” according to Pierre Rochard. He explained:
“Such blocks would be invalid and so can only be created by miners willing to lose the allowed income from having created a block (at least 12.5 XBT or $80,000 USD).”
Similar clients for Bitcoin Cash (BCH) and Litecoin (LTC) were also affected by this bug and users are likewise urged to update their clients. Charlie Lee of Litecoin announced a similar update on September 18 to protect Litecoin clients from the same issues.
At the time of press, over 9,000 nodes are running on the Bitcoin Network of which Bitcoin Core makes up more than 90 percent of this volume.
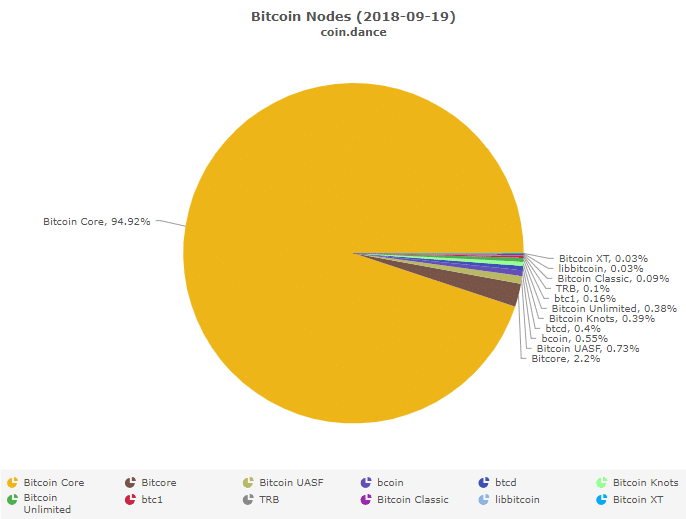
(Source: coin.dance)
Since the announcement, more than 1,000 nodes have updated to 0.16.3 while a handful are at risk despite upcoming attempts to patch older clients. There has also been concern regarding the danger this vulnerability, recently titled “CVE-2018-17144,” poses for Bitcoin’s second layer protocol, the Lightning Network.
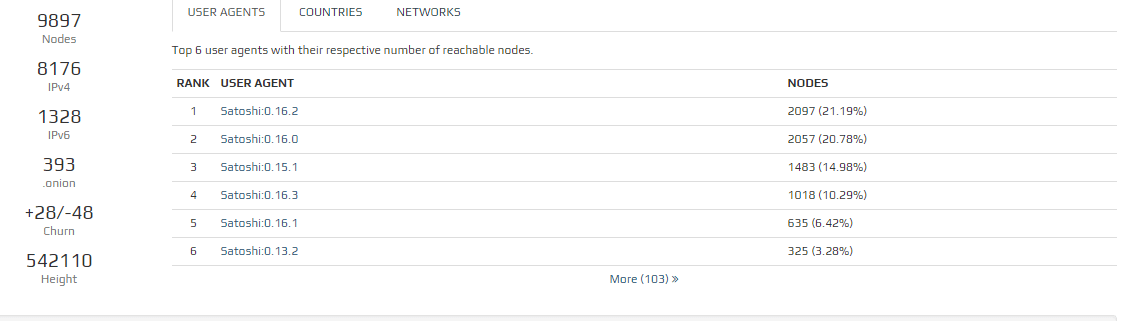 (Source: Network Snapshot)
(Source: Network Snapshot)
Although all funds are technically safe, the downtime inflicted on the network if a block which included an invalid transaction was published, it may also compromise any open state channels between two LN nodes. If a node is down for longer than 24 hours, the exchange peer could potentially steal time locked funds by publishing an outdated state channel. This maneuver is, however, risky as the exchange peer cannot perfectly identify with which node it is communicating.
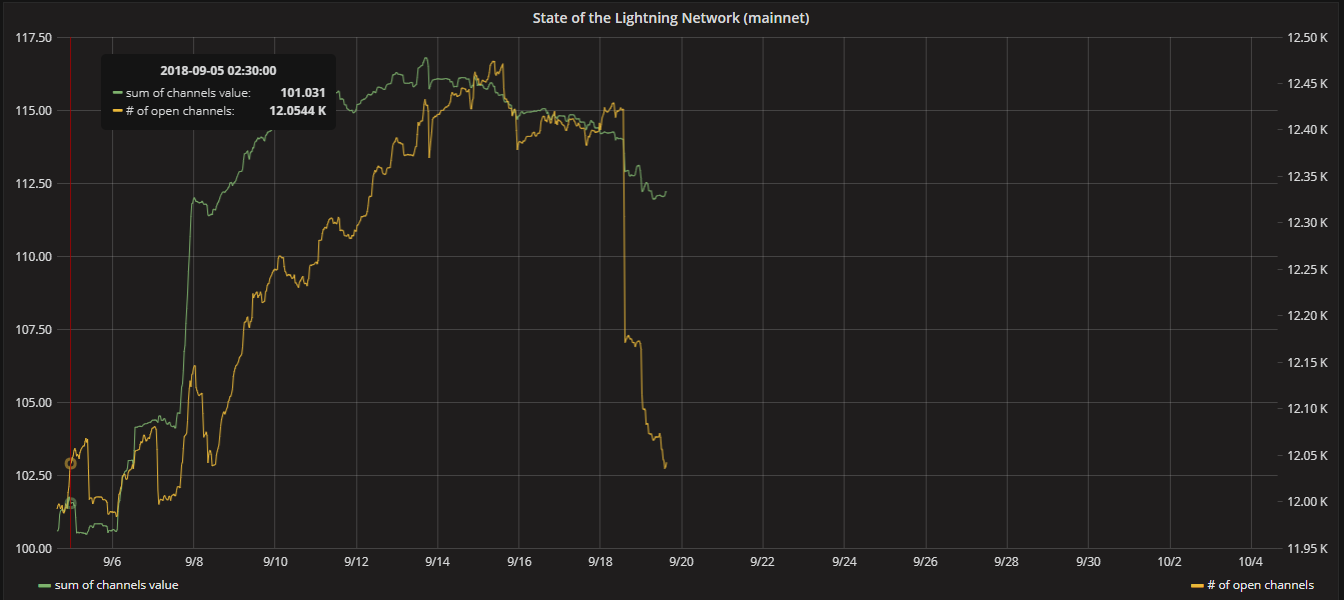
(Source: Grafana)
Consequently, the number of open channels dropped since the announcement on September 18. Keeping a close eye on this metric should also indicate when updated nodes have reopened state channels.















