Bitcoin.org Warns Bitcoin Community of State-Sponsored Attack

Bitcoin.org, a website controlled by individuals selected by none other than Satoshi Nakamoto many years ago, officially released a warning that state-sponsored hackers may tamper with the binaries for the upcoming Bitcoin Core release, version 0.13.0.
When a piece of software is released, users can choose to download the open source version on repository hosting service providers like Github or from distributors like Bitcoin.org. The issue with obtaining software from a distributor is if hackers with powerful and sophisticated malware target the distributor’s website, it could affect the files of the software.
The real danger of the attack surfaces when the website of the distributor fails to guard its assets with necessary resources and security measures. If and when an attacker successfully penetrates the website of the distributor, the attacker can carry out operations to significantly alter the files of software held by the website.
Such change in the core component in software can lead to detrimental effects to the network and users. For instance, downloading a contaminated version of the Bitcoin Core will highly likely lead to users losing funds from their wallets and having their computers and files compromised.
An attack of this caliber can also affect the entire network by launching attacks against the Bitcoin network itself, potentially placing a large number of users vulnerable against theft and loss of funds.
“Bitcoin.org has reason to suspect that the binaries for the upcoming Bitcoin Core release will likely be targeted by state-sponsored attackers. As a website, Bitcoin.org does not have the necessary technical resources to guarantee that we can defend ourselves from attackers of this caliber. We ask the Bitcoin community, and in particular the Chinese Bitcoin community to be extra vigilant when downloading binaries from our website,” said the Bitcoin.org administrators.
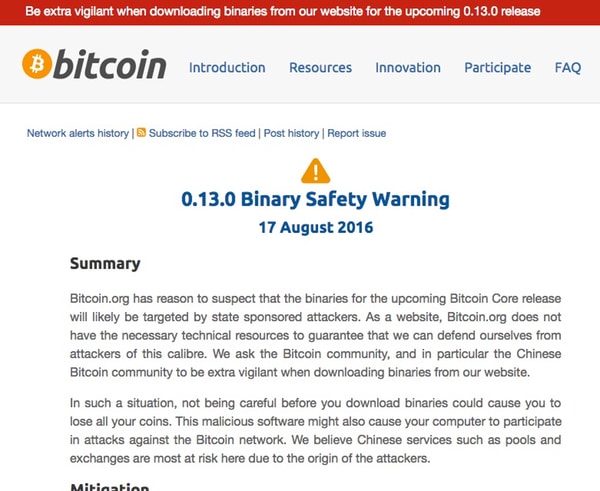
However, the Bitcoin.org team began to receive criticisms from the community after they struggled to identify their reasons behind the suspected state-sponsored attacks. While the Bitcoin.org team states that they have their reason to suspect such attacks, the team hasn’t provided any sort of evidence to support their claims.
Bitcoin Core developer Eric Lombrozo heavily criticizes the maintainer of the Bitcoin.org site for spreading paranoia about the Bitcoin Core binaries themselves.
“The maintainer of the bitcoin.org site (which is unaffiliated with the Bitcoin Core project itself) posted an advisory of an apparent threat he’s been informed about – without consulting anyone else. Why this was done is uncertain, but verifying cryptographic signatures for builds is generally recommended practice in any case,” said Lombrozo. “Perhaps certain sites where people download the binaries could end up getting compromised, but let’s not unnecessarily spread paranoia about the Bitcoin Core binaries themselves.”
Yet, the administrators further emphasized that the Chinese Bitcoin community must be particularly concerned with the anticipated attack and must take necessary steps to securely download binaries or the Bitcoin Core release 0.13.0 from Bitcoin.org.
Based on their statement alone, it can be deduced that the Bitcoin.org team believes state-sponsored attackers are targeting the Chinese Bitcoin community by attempting to alter the files offered by the website. Still, without appropriate evidence, it is difficult to speculate whether this attack will eventually play out as Bitcoin.org anticipates.
Bitcoin.org recommends users to compare the cryptographic signature between the Bitcoin Core 0.13.0 offered by Bitcoin.org and the actual signature used by the Bitcoin Core developers.
“The hashes of Bitcoin Core binaries are cryptographically signed with this key. We strongly recommend that you download that key, which should have a fingerprint of 01EA5486DE18A882D4C2684590C8019E36C2E964,” wrote Bitcoin.org.














