Exploring crypto’s most notorious dark web cybercrime forum

We gained access to BreachForums, a closed online forum with a thriving cybercrime community, to get a sense of the products and services being sold on the digital black market of the dark web.
Here’s what we found.
This article is written for educational purposes, and doesn’t encourage the use of the darkweb.
Table of Contents
What is the dark web?
As a quick bit of background information, let’s clarify what we mean by the dark web and cybercrime forums. The dark web is a hidden part of the internet, accessible only through special browsing software like Tor, that focuses on user anonymity.
The dark web serves as a hub for both legitimate uses, such as privacy-conscious browsing, and illegal activities, including the sale of stolen data, drugs, weapons, services, and other contraband.
Cybercrime forums on the dark web are communities where hackers, fraudsters, and other criminals exchange information, tools, and services, often involving cryptocurrencies to facilitate anonymous transactions.
What is BreachForums?
BreachForums was launched as RaidForums in 2015 by Portuguese hacker Diogo Santos Coelho. RaidForums was started as a community focused on ‘raiding’ websites and online spaces as a form of pranking, trolling, or online disruption.
However, as hackers on the site began breaching social media platforms and websites and stealing millions of user credentials, they started to sell these credentials to the highest bidder. RaidForums quickly evolved into one of the most sophisticated and well-established hubs of organized criminal activity on the dark web.
When Binance was breached in February 2024, BreachedForums was the first place that the user KYC details popped up for sale, and the same was true of the leaked Bitcoin ATM code used in the state of El Salvador, which appeared for sale on BreachForums in April of the same year.
The site started to attract cybercriminals looking to buy sensitive information from corporate security breaches and even leaked government documents, causing it to be the focus of international law enforcement efforts.
In 2022, Europol and U.S. intelligence agencies collaborated to seize the website and identify and arrest founder Diogo Santos Coelho who is now in UK custody awaiting extradition to the US for charges of cybercrime.

RaidForums was quickly re-established as BreachForums by a user called PomPomPurin who was arrested by the FBI in 2023, and the site was taken over by another user called Baphomet. BreachForums was seized by the FBI in May 2024, although cloned versions of the site have since popped up once more.
While the site still boasts strong activity, as we’re about to show, many online users have speculated that the website may be a ‘honeypot’ or trap set up by the FBI to monitor cybercriminals and expose them for prosecution.
What we found on the dark web crime hub BreachForums
Entering BreachForums, we were immediately confronted with a barrage of proposed illegal activity. While some cybercrime forums adopt a more subtle approach of masquerading as communities of IT and cybersecurity enthusiasts, BreachForums has never made any such efforts to hide its true nature, and the home page at the time of our login showed users offering the violent services of the MS13 or La Mara Salvatruca gang for $10,000.
Like all dark web postings involving violence, this is more likely to be a scam than a genuine offer, but the illegal activity didn’t stop there. The scrolling chatbox of the website also displayed users discussing, in real-time, the sale of The forum’s marketplace, which is buzzing with sellers offering illegal products such as stolen data, tutorials on bank fraud and credit card fraud, IP tracking, and much more.
There was also, of course, a thread of Anime and Manga appreciation because even cybercriminals have hobbies.
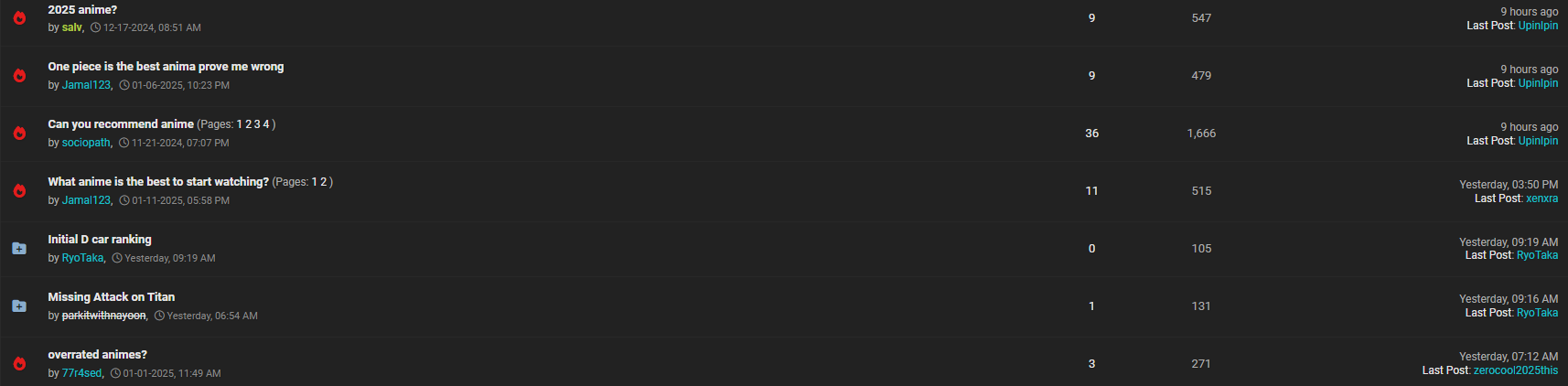
All of the posts shown in this article were posted within hours of our initial login, demonstrating strong activity in an online community that is still very active, although one presumes under heavy observation from law enforcement.
The above image shows users selling access to everything from online video streaming platforms like Paramount Plus and Netflix to breached OnlyFans accounts.
Posts in the leaked data subforum showed users selling data leaks, including bundles of email logins for C-Suite directors of various companies as well as ID documents from the UAE, India, Qatar, and Saudi Arabia, as well as a leak of files and images stolen from Saudi Arabian military emails.
This last leak featuring military documents appears genuine according to our preliminary investigation but was also shown to be from 2016, indicating that this user is attempting to pass off old leaked information as fresh, one of many examples of the types of scams that take place even among cybercriminals online.
One user claimed to have exclusive access to an Australian health insurance MedBank leak, and Australia’s MedBank was indeed breached by Russian cybercriminals in 2022 when the personal information of 9.7m Australians was stolen.

Unlike the hitman-for-hire type posts that the dark web is famous for, these document and identity leaks are sadly very plausible, as the main purpose of BreachForums is indeed to sell stolen data of this nature, and business has been booming for years.
However, with the repeated seizures and arrests by law enforcement, it’s possible that some of these posts are also traps by the FBI or other agencies seeking to catch criminals in the act.
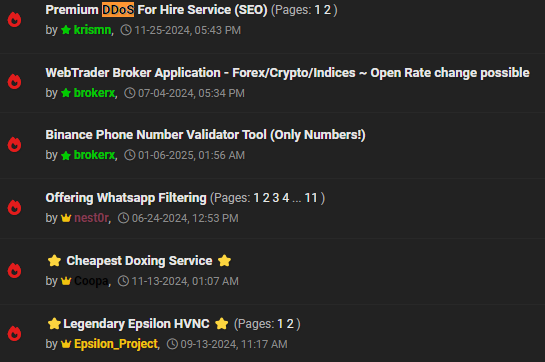
Services found on BreachForums
As well as stolen data, industrious cybercriminals also offer various services for hire on the dark web, invariably taking cryptocurrency as payment.
On BreachForums, we immediately found users purporting to offer DDoS services, access to a distributed denial of service attack where criminals leverage a botnet to shut down a website’s operations to either extort money from the victim, target competing businesses or simply spite an enemy.
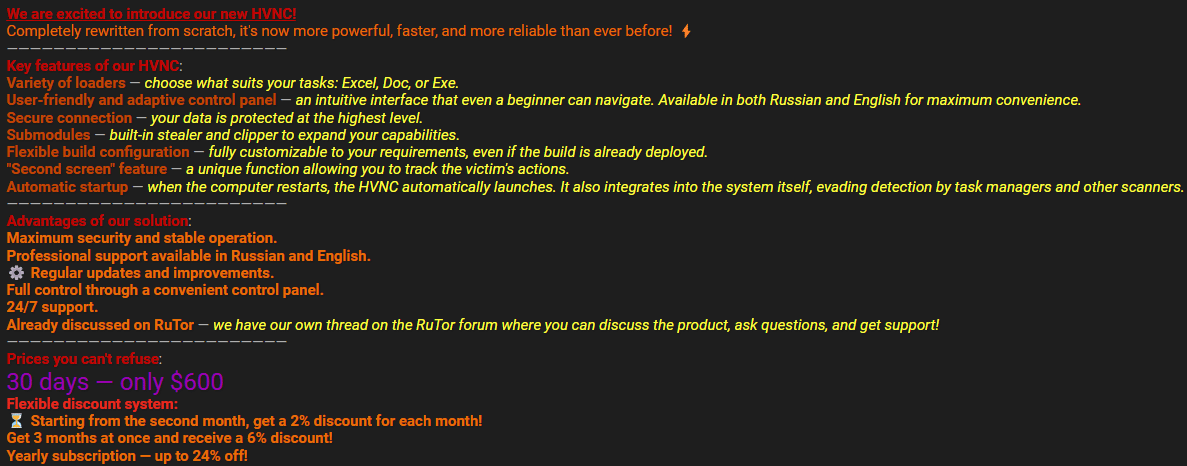
One online group of cybercriminal developers had an advertisement for HNVC or Hidden Virtual Network Computing services that can be used to gain remote access to a victim’s computer.
It was interesting to note that much like an ad for legal online services, the post had a detailed list of features and pricing options available and offered customer support in both Russian and English.
Other services included services to provide phone numbers allowing criminals to receive login codes to activate online accounts without identifying themselves or their own phone number.
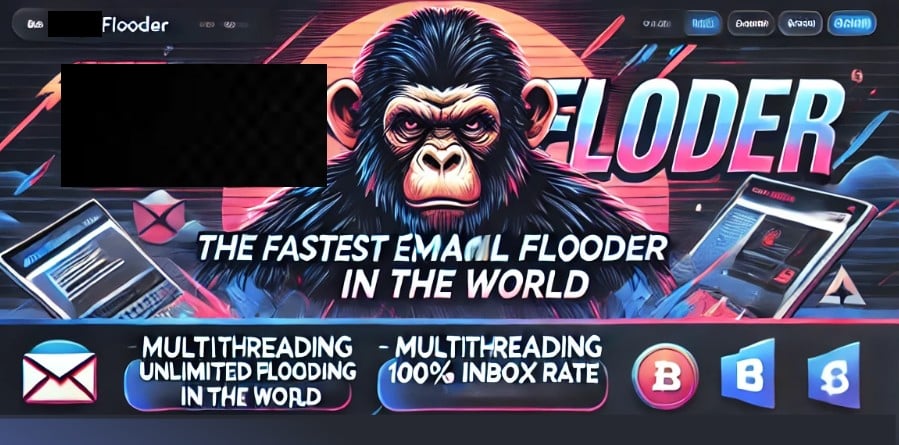
We found bulk email senders used for illegal mass-marketing campaigns for products, phishing scams, or other malware, and also saw advertisements for email flooders used to clog up the email inbox of an enemy in an effort to make the email unusable or to hide malicious activities such as warnings of attempted logins.
One email flooder went to the trouble of creating what appears to be an AI-generated banner ad and logo for their service, the name of which we have censored so as not to advertise their services.
We saw entire threads dedicated to services selling access to remote online servers, programming services for web development, and even graphic design services, all of which could be used to create sophisticated scams such as fraudulent landing pages to steal victim’s user data.
Of course, while some of these services may be legitimate, many of them are likely fake, and due to the website being seized and reopened multiple times, the accounts here are all under two years old.
Cybercrime forums often operate on an escrow basis, or on the basis of trust where a user has a proven track record of ‘honest’ sales, whereas this new website has few measures in place to safeguard against scams.
We did see several services advertising that they accept escrow payments, meaning a vetted third party holds funds until both parties are satisfied with payment, as with this developer offering pre-made phishing websites and landing pages.
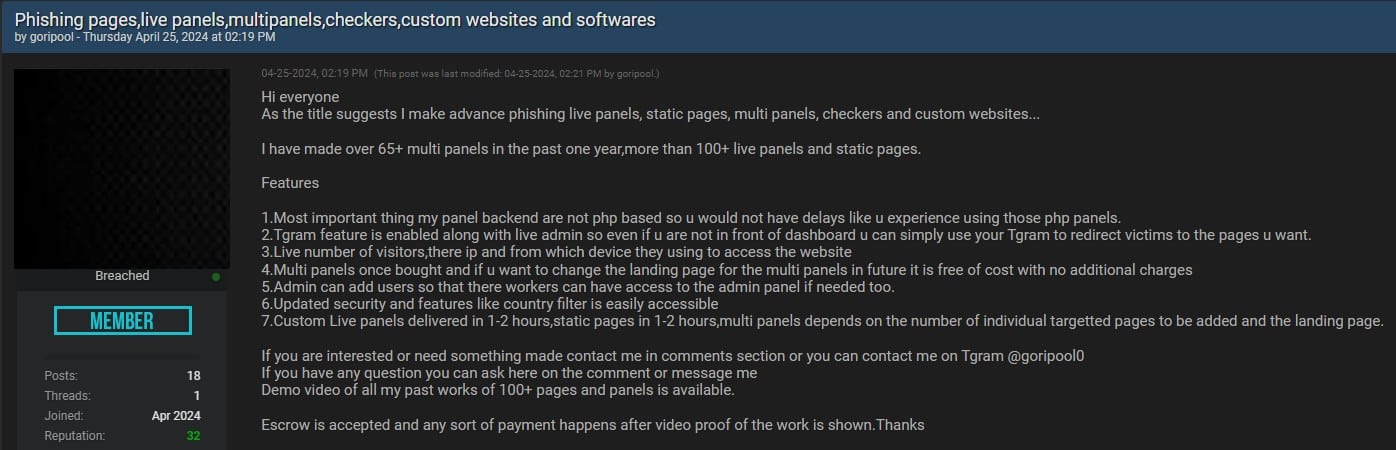
The willingness to accept escrow indicates that this user may indeed be selling what they claim to sell, although there are likely many scams involving escrow payments on this site as well.
In fact, the site has an entire scam thread on the site that shows a log of users reporting on-site scams.
User uuu732 reports that their efforts to scam others online backfired due to falling prey to a scam on BreachForums themselves. They paid user PennyTrate-x $300 for software that would allow them to bypass malware detection softwares and send malware-infected PDFs to their unsuspecting victims.
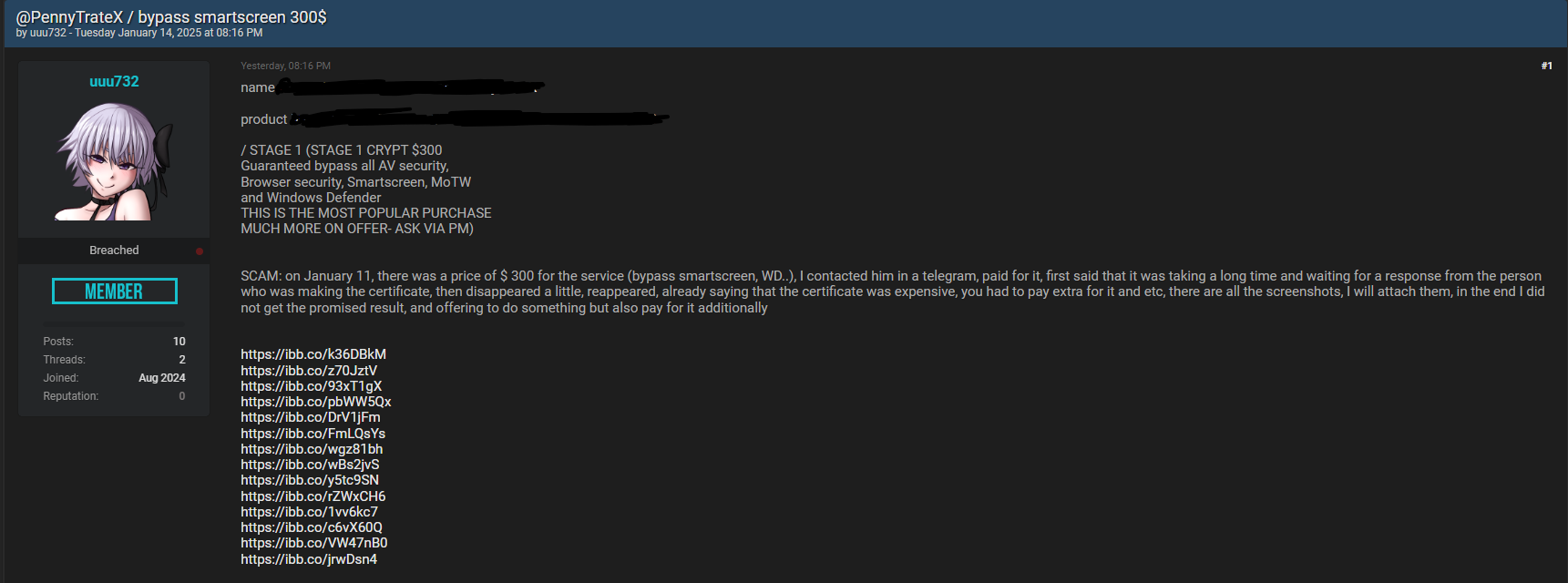
The seller did not provide the goods, and when the moderator asked them for an explanation, they declined to respond, leading to their account getting banned.
Another user reported a dispute with a different seller. In this case, the user spent $500 attempting to purchase database of user credentials breached from a Swiss insurance company and an additional $1,300 trying to purchase the database of a Swiss retail outlet. They reported that they did not receive their illicit data in either transaction.
What do dark web criminals do with stolen user data?
Cybercriminals buy login data and user data in an effort to hack email and social media accounts to either gain access to a user’s finances and rob them, or to gain access to sensitive information that they can further exploit.
For example, a dark net criminal might access a user’s PayPal account and try to make unauthorized purchases or transfer funds directly to another account, or commit identity theft by applying for loans in someone else’s name using their passport information.
This information is also commonly used for extortion and blackmail purposes when criminals find sensitive information by logging into their victim’s accounts.
How to stay safe online
As we can see, the dark web is a dangerous subsection of the internet for many reasons. Even on this website that has been seized and reopened multiple times, we find an open-air bazaar of criminal activity ranging from illegal services and products to scams being perpetrated against other members of the forum.
On the clearnet, users can stay safe by implementing two-factor authentication on their devices and online accounts, meaning a second device like their phone is needed to sign in to an account. This can help prevent hacking and phishing attacks. Likewise, taking care to verify URLs online to ensure that they’re correct and not mispelled or fraudulent can help prevent falling prey to an attack.
Unsuspecting users visiting the dark web, even purely out of personal interest, will find themselves rubbing shoulders with seasoned scammers and hackers probing for any weakness they can find. Users visiting the dark web should avoid clicking on any unfamiliar links or downloading any files, and while it should go without saying, making a purchase of any kind can open you up to all kinds of trouble from both legal and non-legal actors.
In fact, the best way to stay safe from the dark web is simply not to visit it in the first place! Let us do that for you. We aim to visit other corners of the dark web on a regular basis and give regular updates on our findings, keeping you up to date on the underbelly of the global internet.
How to get to the dark web on a Chromebook?
People ask this all the time, and the answer is a little complicated. Firstly, we don’t recommend that anyone accesses the dark web! While the space is interesting to explore from a journalistic point of view, it’s also full of scammers and other types of criminals that can be dangerous to come across. To get to the dark web on a Chromebook, people typically install Linux via the Crostini app and simply add the Tor browser repository to gain access to Tor’s hidden serices, AKA the dark web. However, once again, this is not recommended unless done for research or journalism purposes.
Why is the dark web so creepy?
The dark web has a reputation for being ‘creepy’ partly due to the prevalence of popular YouTube videos which showed YouTubers claiming to open ‘mystery boxes’ from the dark web, as well as the popularity of short stories and ‘creepypastas’ which featured the dark web in horror fiction.
In reality, these videos are typically staged, and the dark web is often more businesslike. People usually access it either to share information without being censored or persecuted, such as political whistleblowers, or, of course, to perpetrate cybercrime and deal in contraband.
How to check my if my email is on dark web?
While breached email addresses are sold on websites like Nulled, you don’t need to access the dark web to see if your email is there. To check if your email is on the dark web, you can use the Have I Been PWNed tool on the clear net instead.
Is the dark web real?
Yes, the dark web is very real! Large sums of money are exchanged in the sale of narcotics, breached online accounts, malware, weapons, hacking services for hire, and other forms of contraband.
What to do if email is on dark web?
If your email is found to be on the dark web, you should change your password immediately and setting up two-factor authentication (2FA). If you’re finding that people are still trying to access your account, such as with emails in your inbox asking you to confirm logins, you might want to consider changing your email address altogether.