Monero Mikrotik Madness: Carrier-Grade Cryptojacking Scheme

There are approximately 200,000 Mikrotik routers that are potentially vulnerable to the latest security breach devised by hackers to install and spread cryptojacking software that mines Monero (XMR).
A team called Bad Packets has been monitoring the spread of the infections ever since the security vulnerability was first reported on August 2, 2018. The vulnerability exists within the management portion of the Mikrotik code and allows attackers complete access to carrier grade routers in use by companies all over the world. Hackers have added the Coinhive cryptominer to Mikrotik routers deployed in countries like Brazil, India, Indonesia, and the United States. This vulnerability allows the injection of the Coinhive miner into machines connecting to the internet through an affected Mikrotik router. Millions of PC’s are at risk with this attack. Simon Kenin, a security researcher with Spider Labs, writes:
“Let me emphasize how bad this attack is. The attacker wisely thought that instead of infecting small sites with few visitors, or finding sophisticated ways to run malware on end user computers, they would go straight to the source; carrier-grade router devices.”
As of an October 1, 2018, paid search on Shodan (paywalled), a security monitoring site, there are 218,126 devices affected by this cryptojacking.
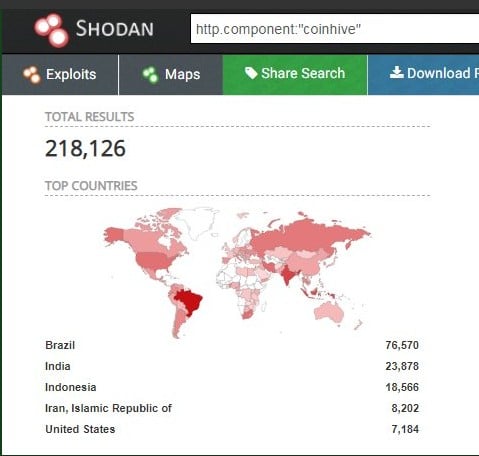 (Source: Shodan)
(Source: Shodan)
The current vulnerability, CVE-2018-14847, is different than the earlier severe weakness first reported in March 2018. The security issue widely reported by the media was called “VPNFilter,” and it could allow any attacker to take over a Mikrotik router with the vulnerability. Mikrotik patched this vulnerability in March of 2017.
The current vulnerability has received virtually no press coverage and has far-reaching implications for all affected Mikrotik operators. Because of this, hackers have taken over more than 200,000 routers and are actively injecting crypto mining malware, packet analyzers, and more. Unlike the VPNFilter loophole, rebooting will not clear the attacker off of the router.
Despite warnings by numerous security researchers, none of the domains utilized by the attackers have been flagged or blocked by major carriers. As told by VriesHd:
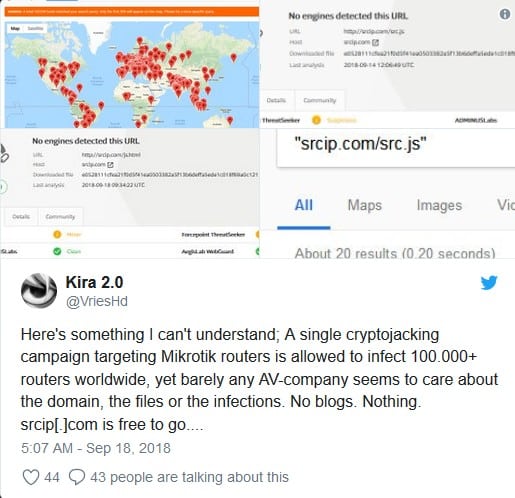
To clear the attacker off of the router, all affected Mikrotik router operators should cleanly upgrade the firmware of the Mikrotik to the latest version (6.43) and to use the most recent Winbox control panel (3.18).
















