Hack! A full Report of the MetaMask Recent (On-Going) Phishing Attempt

On June 7, 2018, User WeaponizedMath reported on Reddit that our site BTCManager was serving a phishing popup that only affected the users of MetaMask browser plugin. We were able to resolve the issue within 24 hours of the report.
PSA: BTCManager.com is running MetaMask phishing software from ethereum
For more info on what Phishing, we recommend the wiki article.
Moreover, we have not heard from anyone saying they lost currency because of it on our site. A big part of this goes to the quick response of the MetaMask team in warning their plugin users. We are also grateful for quick whitelist after the issue was confirmed resolved.
https://twitter.com/metamask_io/status/1005151960142696449
What Was the Phishing Attempt?
Initial investigating found the attacker made a popup clone of MetaMask asking users to restore their vault with their private key due to updates with the extension. It did not steal anything without interaction. A user would have had to put in the private key theirself. Naturally, MetaMask or any other wallet never asks for a user’s seed out of nowhere, ever! It should be noted that we don’t have any method of payment or donation on the site. So, there would be no reason for the plugin to be active. Metamask wrote the following in a related Medium post:
“MetaMask will never spontaneously ask you for your seed words, and is actually totally incapable of popping up in the top right without the user clicking the fox (as are all WebExtensions)! If you ever see this kind of popup on a site, contact us immediately!”
The further we dig into what happened it becomes more and more evident that this issue was an exploit of a well-planned and experienced attacker. When looking across many websites, they all point back to a DigitalOcean IP.
We have to be careful on just what information we release about the hack to prevent natural copycats. However, any security experts or other qualified individuals that would like to help continue the investigation, please reach out. We are still working on trying to prevent this from happening to countless other Cloudflare users.
How Did the Phishing Code Get on BTCManager?
The attacker was able to make two small hard to notice changes to our Cloudflare account. Through API they created a new sub-domain that we have used before called img.btcmanager.com. The sub-domain directed requests to their server. Then using page rules, they merely redirected two JS requests to their copy of the Javascript. The Javascript included the phishing code and remaining redirects involved.
We did not pick up on this sooner because as far as the browser and any scanners, we merely moved some of our resources offsite. Moving content offsite is a common practice for websites to help distribute web load among other things. Scanners that we use on an ongoing basis had absolutely no reason to think anything was wrong especially since this was brand new code and a zero-day phishing attempt against Metamask.
What about Basic Security?
At this point, I can hear the screaming “How could you let this happen? How did they gain access to the Cloudflare account? DON’T YOU USE 2-FACTOR?”
The answer is startlingly simple and brings to light a critical problem with Cloudflare. The hacker was able to obtain our Cloudflare API key (still are not sure how). We use this key to control caching from the website so that we can push changes to the users in a quick manner while maintaining the use of their servers. We deliver terabytes of data a month to our users. Most of this (80 percent+) of the data comes to you from cached versions on Cloudflare servers, which saves us tons on server costs. It also means that if you live in a different country than our servers the website still loads very quick. Without Cloudflare’s network, this would cost hundreds more a month.
To get a decent idea of what an API is take a look at this article.
The critical issue is Cloudflare has absolutely no way to turn off the API or limit what it can do. Ultimately, we may have to quit Cloudflare services for the time being and advocate others to do so as well until this issue can be cleared up. The API can change or control every aspect of Cloudflare remotely. It makes no difference that every admin and editor is required to have 2-Factor authentication (Not phone 2-factor. Real 2-factor. Don’t use phone SMS 2-factor, it is super insecure.) Including the email and all sever accounts associated with the website.
The hacker was able to bypass all of our security precautions with what is essentially a username and password that we cannot turn off.
We are sad about this change as Cloudflare provides a lot of excellent services such as DDOS protection (We have been attacked with by DDOS dozens of times in the last six months), IP protection and, of course, the caching and speed improvements. However, we don’t see another option. That said, the Cloudflare support team has been quick to respond and help in what way they can. However, they don’t seem to have a grasp on just how big of an issue this is.
How Do I Protect my Crypto? I Have to Use a Hot Wallet
First I want to say that we do not think you should quit using MetaMask or other similar wallets. Just understand the risks involved. If they are too great, start using multiple levels of wallets, such as hardware wallets to protect the bulk of your crypto.
The problem with protecting crypto is you have to continually fight between security, function, and ease of use. Browser wallets and phone wallets are known as hot wallets. While they can be excellent for using every day, they are the most vulnerable to attacks like this and many others.
Most websites can see all the plugins you use. The best thing to do, at current, is not browse or use the internet with the same browser your wallet is on. Install multiple browsers, save one for regular use and keep the second browser secure for sensitive operations. This latter browser, should only be used on limited basis with verified pages and the plugins. Do not download extra plugins. You can even use a portable version of Firefox and keep it on a thumb drive. This technique is also good practice for banking and other types of online financial transactions. Rarely should email even be opened on this browser.
What Can I Do to Prevent Getting my Site Hacked this Way?
Unfortunately, if you use Cloudflare, you are at risk even if you never used their API. We use the API for limited things as described above. Others that have been hacked in the same way swear they never use the API for any reason. Until Cloudflare fixes this issue or we switch, we have instituted a policy of switching the API keys on a very regular basis.
As always, using 2-factor, password managers, never using the same passwords, not using autofill for passwords and changing passwords regularly help keep these accounts safe. We recommend and practice switching all essential passwords every three months, all important ones every six months and all passwords at least every 12-18 months.
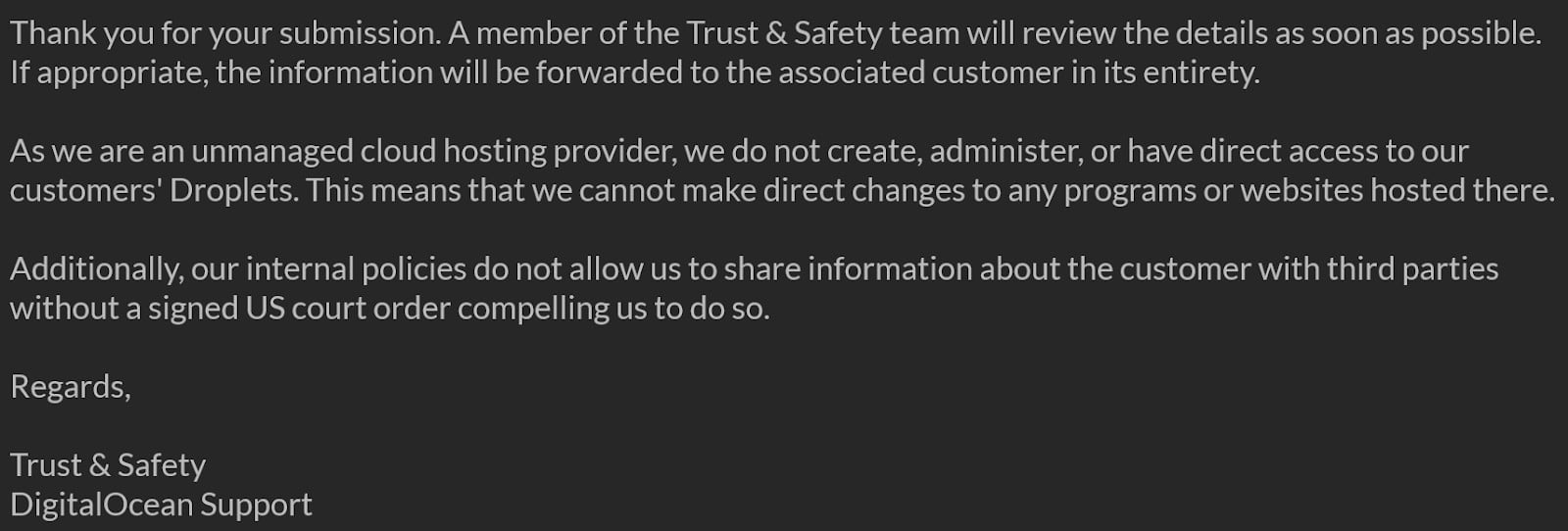
What about DigitalOcean and the Hackers Servers?
Currently, DigitalOcean has not helped at all and seem to be ok with the fact that they are being used to serve up phishing attempts. This is based on the variety of response they have given us. We can’t say anything more on the subject except the MetaMask has confirmed they are using their resources and experience to fight DigitalOcean to shut the hacker down and possibly find out who is behind it.
In closing, we want to make a big thanks to user WeaponizedMath for reporting and helping save crypto from theft. We hope you continue to read BTCManager as a crypto news source. We are honored that someone felt we were big enough to deserve first use of a zero-day attack. We promise to continue to keep the site up to date and actively do our very best prevent our readers from being in danger while using our site.
P.S. We’ll say it once more. If you have the skills to help track this guy down, we know MetaMask and BTCManager would be more than happy to have your help.