Review of 5 recent API hacks in crypto: decentralization’s weak point

In software engineering, API stands for Application Programming Interface. It can be understood as a proxy that allows two different software entities (user and platform or two applications) to communicate. It defines methods and data formats software applications can use to request and exchange information.
API instruments are used here and there in crypto: digital assets exchange, trading bot, and on-chain wallet leverage APIs to interact with blockchains and end users.
As such, any problem with API, including delays in data processing or “man-in-the-middle” attacks, can result in significant data and asset losses.
API hacks: why are they happening?
In general, there are too many attack vectors in crypto APIs. Let’s check out the most common attack designs malefactors use to obtain crypto assets and data:
- Exposed API keys or vulnerable endpoints: hackers may bypass security mechanisms with modified or stolen API keys.
- Man-in-the-middle (MITM) or replay attacks: malicious actors can intercept communications between fair actors or use the same key repeatedly to access larger instruments.
- DoS attacks: Some platforms might need robust rate-limiting mechanisms. Attackers can exploit this by overwhelming the system with API requests, leading to denial of service (DoS). During such times of vulnerability, other attack vectors might also be pursued.
As such, the attacks on API instruments might result in several dangerous effects for crypto apps, including the likes of
- Price manipulations;
- Attackers directly steal assets;
- Large-scale data leaks;
- And so on
In 2022-2023, direct losses from attacks on crypto APIs reached hundreds of millions of USD. Both security experts and hackers created increasingly sophisticated protection and attack tools.
Top 5 API hacks in web3
In recent months, dozens of crypto protocols have been targeted by API exploits. Below is a brief recap of this nature’s most significant and large-scale hacks.
OpenSea API leak: third-party data breach
On September 23, 2023, OpenSea, a top-tier non-fungible tokens (NFTs) marketplace, announced that some API keys were compromised due to a “third-party security breach.” The OpenSea team immediately asked all its API customers to rotate their keys.
The team announced that the keys that remain untouched were forcefully sunset on October 2. OpenSea kept silent about the name of the attacked “provider” and the number of customers affected.
Nansen API leak: supplier error affected 7% of users
A few hours after the OpenSea announcement, Nansen, a leading analytical and research firm, informed its users about a similar accident. According to its statement, over 6.8% of Nansen API users suffered the hack.
Email addresses, blockchain wallet public addresses, and password hashes were leaked. Nansen also didn’t disclose the name of the affected “third-party” platform but added that it was a Fortune 500 company, and the first reports about the hack were published on September 20. It is still unclear whether the Nansen and OpenSea incidents were somehow related.
General Bytes API leak: largest crypto ATMs network under fire
General Bytes, a prominent network of Bitcoin ATMs worldwide, announced on March 28, 2023, that an attacker had remotely uploaded their Java application via the master service, exploiting a zero-day vulnerability ten days prior.
The cyber-criminals could read and decrypt API keys to access funds in hot wallets and exchanges. They successfully drained General Bytes’ storages of $1.5 million worth of Bitcoin and other major altcoins.
Coinbase API leak: a hack that never happened
In February 2022, Coinbase, a leading U.S. crypto exchange, disclosed a serious API vulnerability. The platform even halted deposits and withdrawals to fix the bug unveiled. This flaw would have allowed an attacker to take over user accounts.
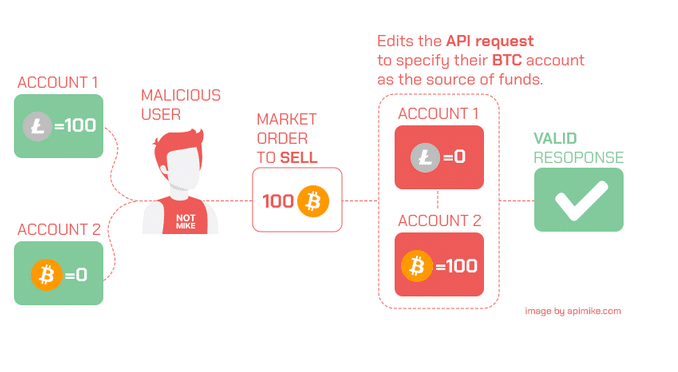
Per the experts in API security, the vulnerability had been allowing the malefactors to edit API requests to steal money from Coinbase storages.
The exchange awarded a whopping $250,000 bug bounty to cyber-security researchers for disclosing the breach that was never exploited.
Skyrex API leak: attacking top crypto exchange Binance
In mid-November 2022, some Binance users unveiled that the positions from their accounts were opened and closed by third parties without authorization. Skyrex, an AI-powered trading bot, leaked the API keys.
Skyrex customers permitted the bot to trade on their behalf using the funds stored in their Binance accounts.
Unfortunately, some malicious individuals could access the funds of a seasoned NFT enthusiast and use them to close his long position in the AXS/USDT pair.
The exact amount of the losses suffered by the customer has not been disclosed.
Enhancing API security with access tokens: the case of GetBlock
As API hacks in 2022-2023 stole all the headlines and resulted in dramatic data and money losses, many established web3 teams decided to reconsider their security layers.
RPC node provider GetBlock, a platform that connects decentralized applications (dapps) to blockchains, announced the access tokens release, its crucial security upgrade.
Access tokens were added on Oct.24, 2023.
With the latest upgrade now deployed, customers can use access tokens as their primary authentication tool. Access tokens have replaced API keys to provide better security and usability.
The new solution can reduce potential attack surfaces and streamline mitigating hypothetical losses.
For example, suppose a user’s access token is compromised instead of creating new API keys for all chains, networks, and interfaces.
In that case, they can rotate their access tokens with just one click. This makes the process faster, easier, and more secure.
Also, GetBlock’s access tokens dramatically increase the customizability and transparency of blockchain connection for all dapps running on GetBlock’s BaaS nodes.
Bonus: tips to stay safe
Here are five rules for crypto enthusiasts to shield themselves from potential API hacks:
Guard your API keys
- Never share publicly: Accidentally pasting your API key on forums, social media, or platforms like GitHub is akin to leaving your house keys on your front porch.
- Limit access: When generating an API key, use the principle of least privilege. This means giving critical access only to the features it needs.
For instance, if you’re using a trading bot for price analysis only, there’s no reason it should have permission to make trades or withdrawals.
Use a dedicated and secure connection
- HTTPS always: make sure to use a service or platform that operates over HTTPS, which encrypts data between your computer and the server, making man-in-the-middle attacks more difficult to execute.
- VPN benefits: consider using a VPN when accessing crypto platforms or working with APIs.
This extra layer of encryption is essential when using public networks.
Regularly rotate and review API keys
- Change them up: treat API keys like passwords. Periodically changing them reduces the chance that an older, potentially compromised key can be used against you.
- Audit and monitor: frequently review the activities associated with your API keys.
If you notice unfamiliar or suspicious actions, revoke the key immediately.
Two-factor authentication (2FA) is mandatory
- Double the defense: always enable 2FA for any platform or service that supports it, especially those where you generate and use API keys.
This means that even if an attacker gets your key, they’ll have difficulty using it without the second authentication factor.
Stay updated and educated
- Security news: follow crypto news and join online communities. Often, vulnerabilities or potential threats are discussed in these circles, and staying informed will allow you to take precautions early on.
- Platform updates: ensure that any application or platform you use (especially if it’s self-hosted, like some trading bots) is regularly updated. Developers frequently release security patches in response to known vulnerabilities.
Remember, the crypto world is lucrative not just for enthusiasts and investors but also for cyber-criminals. Staying vigilant and proactive in your security practices is the best defense against potential API hacks.
Bottom line
API attacks are part of the daily routine of the cryptocurrency segment. Dozens of exchanges and trading bots are being exploited via API designs. API users should be cautious about their keys and interacting with third parties.
Disclosure: This content is provided by a third party. Neither crypto.news nor the author of this article endorses any product mentioned on this page. Users should conduct their own research before taking any action related to the company.













